How to Create a Private SSH Key for SourceTree
To create a private SSH key for SourceTree, follow these steps:
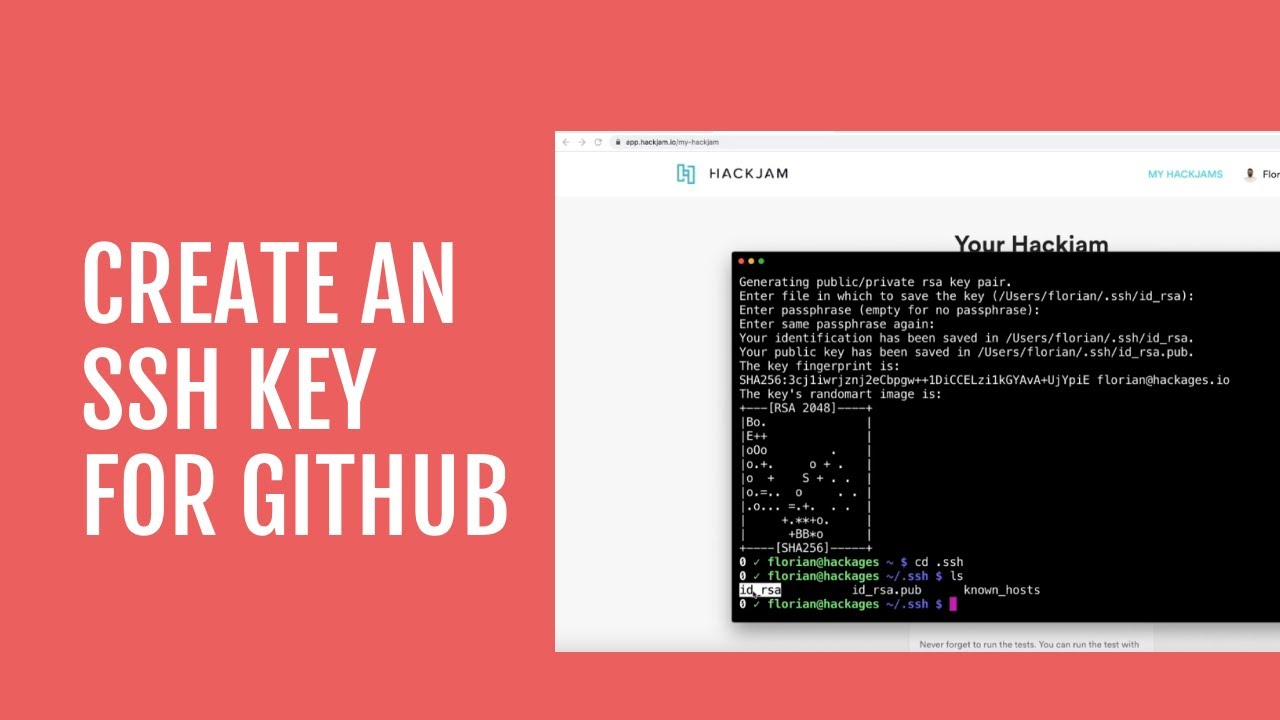
In Terminal, generate a new SSH key using the following command:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com"
Enter a passphrase when prompted, and then press Enter.
The SSH key will be saved in the .ssh directory in your home directory.
In SourceTree, go to Preferences > Accounts > SSH Keys.
Click the Add button and select the SSH key you just created.
Enter the passphrase for the SSH key when prompted.
Click the OK button.
Your SSH key is now added to SourceTree and you can use it to authenticate to remote repositories.
How to Create a Private SSH Key for SourceTree
Creating a private SSH key is an essential step for securely connecting to remote Git repositories. Here are six key aspects to consider when creating a private SSH key for SourceTree:
- Key generation: Use a strong passphrase and a key length of at least 4096 bits.
- Key storage: Store your private key in a secure location, such as a password manager.
- Key management: Keep your private key up to date and revoke access if it is compromised.
- Authentication: Use your private key to authenticate to remote repositories via SSH.
- Authorization: Configure access permissions for your SSH key on the remote repository.
- Troubleshooting: Diagnose and resolve any issues that may arise when using your SSH key.
By following these key aspects, you can create a secure and reliable SSH key for use with SourceTree. This will allow you to securely connect to remote Git repositories and manage your code.
Key generation
When creating a private SSH key for SourceTree, it is important to use a strong passphrase and a key length of at least 4096 bits. This is because the strength of your SSH key is determined by two factors: the strength of the passphrase and the length of the key. A strong passphrase is one that is at least 12 characters long and contains a mix of upper and lowercase letters, numbers, and symbols. A key length of 4096 bits is considered to be secure against brute-force attacks.
Using a weak passphrase or a short key length can make your SSH key vulnerable to attack. If an attacker is able to guess your passphrase or brute-force your key, they will be able to access your remote repositories and steal your code.
Therefore, it is important to take the time to create a strong SSH key. This will help to protect your code from unauthorized access.
Key storage
Storing your private SSH key in a secure location is essential for protecting your code from unauthorized access. If your private key is compromised, an attacker could use it to access your remote repositories and steal your code.
There are a number of different ways to store your private SSH key securely. One option is to use a password manager. A password manager is a software program that allows you to store your passwords and other sensitive information in an encrypted format. This makes it much more difficult for attackers to access your private SSH key, even if they are able to compromise your computer.
Another option is to store your private SSH key on a hardware security module (HSM). A HSM is a physical device that is designed to store and protect cryptographic keys. HSMs are very secure, and they are often used to store the private keys of large organizations.
No matter which method you choose, it is important to store your private SSH key in a secure location. This will help to protect your code from unauthorized access.Key management
Effective key management is crucial for maintaining the security of your SSH key. This involves keeping your private key up to date and revoking access if it is compromised.
- Regularly update your private key: SSH keys can become compromised over time, so it's important to regularly update your private key. This will help to ensure that your key is not vulnerable to attack.
- Revoke access to your private key if it is compromised: If you believe that your private key has been compromised, you should immediately revoke access to it. This will prevent unauthorized users from accessing your remote repositories.
By following these key management practices, you can help to protect your code from unauthorized access.
Authentication
When you create a private SSH key for SourceTree, you are creating a secure way to authenticate to remote repositories. SSH (Secure Shell) is a cryptographic network protocol that allows you to securely connect to a remote computer. When you use SSH to connect to a remote repository, you are using your private key to prove your identity to the server. This ensures that only you can access your remote repositories.
Using a private SSH key is much more secure than using a password to authenticate to remote repositories. Passwords can be easily guessed or stolen, but a private SSH key is much more difficult to compromise. This is because your private SSH key is stored on your computer, and it is not transmitted over the network when you connect to a remote repository.
If you are serious about securing your remote repositories, then you should create a private SSH key and use it to authenticate to remote repositories. This will help to protect your code from unauthorized access.
Authorization
Once you have created a private SSH key for SourceTree, you need to configure access permissions for your SSH key on the remote repository. This will ensure that only you can access your remote repositories using your SSH key.
To configure access permissions for your SSH key on the remote repository, you will need to add your SSH key to the authorized_keys file on the remote server. The authorized_keys file is a list of SSH keys that are allowed to access the remote repository. To add your SSH key to the authorized_keys file, you can use the following command:
ssh-copy-id user@remote_server
You will be prompted to enter your password for the remote server. Once you have entered your password, your SSH key will be added to the authorized_keys file and you will be able to access the remote repository using your SSH key.
Configuring access permissions for your SSH key on the remote repository is an important step to ensure the security of your remote repositories. By only allowing your SSH key to access your remote repositories, you can help to prevent unauthorized users from accessing your code.
Troubleshooting
Creating a private SSH key for SourceTree is an important step to enhance the security of your remote repositories. However, issues may arise when using your SSH key. Understanding how to troubleshoot and resolve these issues is crucial to maintain a seamless workflow and protect your code.
- Identifying Connection Problems:
Troubleshooting SSH key issues often begins with examining connection problems. Verify that your SSH client is correctly configured and that you have a stable network connection. Check if firewalls or other network restrictions are blocking the SSH connection.
- Incorrect Key Permissions:
Ensure that your private SSH key has the correct permissions. The key should be readable only by you (chmod 400). Incorrect file permissions can prevent SourceTree from accessing the key.
- Mismatched SSH Keys:
SourceTree may encounter issues if the public SSH key registered on the remote repository does not match the private key you are using. Double-check that the public key is correctly added to your remote account.
- Outdated SSH Keys:
SSH keys can become outdated or compromised over time. If you encounter persistent issues, try generating a new SSH key pair and updating it on both your local machine and the remote repository.
By addressing these common issues, you can effectively troubleshoot and resolve problems that may arise when using your SSH key with SourceTree. This ensures a secure and reliable connection to your remote repositories, allowing you to manage your code with confidence.
Frequently Asked Questions
This section addresses common questions and concerns regarding the creation and usage of private SSH keys for SourceTree.
Question 1: Why is it important to create a private SSH key for SourceTree?Private SSH keys enhance the security of your remote repositories by providing an additional layer of authentication. They prevent unauthorized access to your code and protect it from potential breaches.
Question 2: What is the recommended key length and passphrase strength for an SSH key?For optimal security, a key length of at least 4096 bits and a strong passphrase are recommended. Complex passphrases consisting of a mix of upper and lowercase letters, numbers, and symbols provide robust protection against brute-force attacks.
Question 3: Where should I store my private SSH key?Store your private SSH key in a secure location, such as a password manager or a hardware security module (HSM). Avoid storing it in plain text files or easily accessible locations to prevent unauthorized access.
Question 4: How can I troubleshoot issues related to SSH key usage in SourceTree?Common issues include incorrect key permissions, mismatched SSH keys, and outdated keys. Verify file permissions, check if the public key matches the private key, and consider generating a new key pair if necessary.
Question 5: Is it safe to share my private SSH key with others?Sharing your private SSH key compromises the security of your remote repositories. Avoid sharing your key, and if it becomes necessary, revoke access immediately to maintain the integrity of your code.
Question 6: How can I revoke access to my SSH key if it is compromised?In case of a compromised SSH key, revoke access promptly to prevent unauthorized usage. Update your SSH key pair, and remove the compromised key from the authorized_keys file on the remote server.
By understanding these frequently asked questions, you can effectively create and manage private SSH keys for SourceTree, ensuring the security and integrity of your remote repositories.
Conclusion
In summary, creating a private SSH key for SourceTree is a crucial step in safeguarding the security of your remote repositories. By following the outlined best practices, you can effectively generate, store, manage, authenticate, and troubleshoot SSH key-related issues.
Remember to prioritize key security by using strong passphrases and appropriate key lengths. Store your private key securely and manage access permissions diligently to prevent unauthorized access. By adhering to these measures, you can maintain the integrity of your code and ensure the protection of your sensitive data.
The Ultimate Guide To Application/json Postman Integration
The Ultimate Guide To Line VTY Cisco Configuration And Troubleshooting
Ultimate Guide To Crime Circumstances: Definitions, Consequences, And Prevention
![How to SSH Through Bastion With Key [Tutorial]](https://i2.wp.com/discover.strongdm.com/hs-fs/hubfs/Imported_Blog_Media/605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key-2.jpg?width=1950&height=1095&name=605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key-2.jpg)
How to SSH Through Bastion With Key [Tutorial]

Create SSH keys in the Azure portal Azure Virtual Machines
How to create and configure an SSH Key for Github & how to create a